[ad_1]
As Log4J and SolarWinds have confirmed, assaults on the software program program present chain are increasingly more frequent and devastating to every the personal and public sector. The Division of Safety (DoD) and its commerce companions moreover face these risks. In its 2021 State of the Software program program Present Chain report, Sonatype reported 12,000 cyber assaults geared towards open-source suppliers, a 650 p.c enhance from the 12 months sooner than. Almost all providers or merchandise that an organization acquires are supported by or built-in with data experience that options third-party software program program and {{hardware}} components and corporations. Each represents a attainable provide of cybersecurity hazard.
For lots of organizations, practices and selection elements essential to monitoring and managing present chain risks are scattered. Security and supplier hazard administration often lie exterior of program hazard administration, and DoD acquisition practices now we’ve got seen current components of this data detailed in numerous paperwork, such as a result of the Program Security Plan (PPP), Cybersecurity Method Plan, System Enchancment Plan, Present Chain Hazard Administration Plan, and Assertion of Work.
Consequently, environment friendly cyber risk-management actions undertaken all by way of the group must be addressed collaboratively all through the lifecycle and supply chain. Moreover, to be taken critically, these risks must be built-in with program hazard administration. Doing so will help relieve the current institution whereby the actions of isolated stovepipes lead to inconsistencies, gaps, and gradual response at biggest. On this submit, I introduce the Acquisition Security Framework (ASF), which helps organizations decide the essential touchpoints wished for environment friendly present chain hazard administration and describes a set of practices wished for proactive administration of present chain cyber hazard.
As we communicate’s Threat Panorama
As we communicate’s strategies are increasingly more software program program intensive and complex, with a rising reliance on third-party experience. By way of reuse, strategies will likely be assembled faster with a lot much less enchancment worth. Nonetheless, this technique carries elevated hazard. All software program program accommodates vulnerabilities which might be laborious adequate to deal with immediately. Inheritance by way of the supply chain will improve the administration challenges and magnifies the possibility of a attainable compromise. In addition to, suppliers can develop into propagators of malware and ransomware by way of choices that current automated updates.
The provision chain intersects the acquisition and enchancment lifecycle at many elements. The DoD and totally different organizations need an built-in focus all through engineering, enchancment, and operations to reduce the possibility of vulnerabilities and enhance security and resilience. A whole lot of system enchancment is now assembly of third-party experience, with each half a decomposition of parts collected from totally different sub-components, industrial merchandise, open-source components, and code libraries. These parts are ceaselessly hidden from the acquirer, resulting in components of unknown provenance, unknown top quality, and unknown security. An attacker’s capabilities to achieve and leverage obtainable vulnerabilities will improve exponentially yearly.
The types of present chains that will impression a system embody the subsequent:
- {{hardware}} present chains
- conceptualize, design, assemble, and ship {{hardware}} and strategies
- embody manufacturing and integration present chains
- service present chains
- current firms to acquirers, along with information processing and web internet hosting, logistical firms, and help for administrative options
- software program program present chains
- produce the software program program that runs on necessary strategies
- comprise the group of stakeholders that contribute to the content material materials of a software program program product or which have the possibility to vary its content material materials
- use language libraries and open provide components in enchancment
With lots hazard distributed and embedded all by way of an acquisition present chain, typical segmented administration approaches no longer suffice. Bigger rigor is required to satisfy the requirements for a program to have environment friendly present chain hazard administration. A typical acquisition integrates quite a few types of approaches for experience inclusion as follows, primarily ignoring the vulnerabilities inherited from each ingredient that is rising cybersecurity hazard:
- formal acquisition and contracting language, along with requests for proposal responses and negotiated outcomes bounded by worth and schedule
- industrial off-the-shelf purchases of present third-party merchandise that embody persevering with service agreements for updates and fixes
- informal selection that entails downloads from open provide libraries, along with code extracted from prior variations or comparable initiatives
In prior publications, I harassed the significance of creating a cybersecurity engineering method that integrates with the software program program present chain to find out and deal with the potential threats that impression an acquisition. It is equally very important to efficiently translate the method into requirements and practices for determining how an acquisition addresses security and resilience risks all through the lifecycle and supply chain. Put one different means, the next logical piece that we should always cope with is implementing a diffusion of environment friendly practices for the acquisition’s present chain hazard administration. ASF provides the framework of what these practices should embody. The framework defines the organizational roles that ought to efficiently collaborate to engineer systematic resilience processes to stay away from gaps and inconsistencies. It moreover establishes how an organization ought to ensure it has environment friendly present chain hazard administration that helps its mission and targets. The ASF accommodates confirmed and environment friendly targets and practices, and it is according to present chain hazard administration pointers from the Worldwide Group for Standardization (ISO), Nationwide Institute of Necessities and Know-how (NIST), and Division of Homeland Security (DHS).
Now we’ve got structured ASF to facilitate the enhancement of strategies enchancment and administration processes to permit greater administration of cybersecurity and software program program hazard. This enchancment at risk administration helps reduce the impression of disruptions and cyber assaults on the acquired system’s means to achieve its mission. The ASF is purpose-built to supply a roadmap for strategies resilience that leverages a confirmed set of built-in administration, engineering, and acquisition major practices. The ASF is designed to
- deal with hazard by way of collaboration amongst acquisition people and suppliers
- facilitate the identification and administration of hazard by making use of major practices which may be tailored to satisfy the needs of the acquisition
Inside an acquisition, program administration establishes the governance for present chain hazard and supplier-management buildings and helps the relationships between this technique and supplier; and engineering integrates the supplier components, devices, firms, and capabilities into the system beneath enchancment. Too many organizations try and separate each of these as within the occasion that they operated independently, nonetheless environment friendly supplier hazard administration requires shut collaboration. For as we communicate’s combination of experience to hold out efficiently, it must be coordinated, verified, and linked by way of present chain hazard administration. Additional challenges of present chain hazard come up for organizations implementing DevSecOps, the place numerous the develop steps are automated by way of the utilization of third-party devices and software-driven processes, further rising the impression of vulnerabilities from these components whereas often decreasing the visibility of the processes to oversight.
On this new actuality, organizations ought to someway deal with the supplier hazard of each built-in piece that they buy, nonetheless the visibility of that hazard is unfold all through many organizational roles. By way of ASF, we’re working to supply organizations a framework to mix the work of these roles in the direction of the frequent function of supporting present chain hazard administration.
SEI Experience Addressing Challenges to Supplier Hazard Administration
In a 2010 SEI evaluation problem, we found that few organizations considered present chain hazard contained in the acquisition and enchancment lifecycle previous a narrowly outlined vetting of the supplier’s capabilities on the time of an acquisition. This failure to consider the duties the acquirer wanted to imagine based totally on the lifecycle use of the third-party product left the group open to an intensive fluctuate of cyber hazard that elevated over time. In later evaluation, we investigated the lifecycle issues with supply-chain hazard and acknowledged that the operational and mission impression of cyber hazard will improve as organizations develop into further relying on suppliers and software program program.
Our experience indicated that acquisitions embody extended lists of requirements in an announcement of labor (SOW) and assume a contractor will adhere to all of them. Each essential helpful and non-functional house (along with safety, cybersecurity, and anti-tamper) specifies a diffusion of splendid needs that assume that the acquired system shall be constructed to satisfy these needs without any consideration of how these quite a few gadgets ought to work collectively. Nonetheless, the vendor will primarily make sure that the system (along with {{hardware}}, software program program, and group interfaces) shall be constructed to be cost-efficient in leveraging obtainable components that meet helpful needs. Verification that the delivered system meets helpful requirements will happen all through testing. Affirmation that non-functional requirements are met will depend on the certification mandates. No one at current has the responsibility to make it possible for the supply-chain hazard is sufficiently low in all factors.
If shopping for organizations use solely testing to substantiate that requirements have been met, they’ll see solely what they chose to substantiate. It is a drain on property to test for every requirement, so an technique that integrates core proof is required.
In too many organizations, it is assumed the contractor manages all important supply-chain hazard. The shopping for group has no visibility into the subcontractor relationships and is unable to substantiate that the primary contractor is imposing the requirements designated inside the SOW on system subcontractors, usually because the primary contractor has not achieved so. By way of our work, now we’ve got found that in numerous circumstances the subcontractors have not acquired the requirements and subsequently have not adopted them.
The Acquisition Security Framework
As acknowledged earlier, the Acquisition Security Framework (ASF) is a set of practices for setting up and dealing protected and resilient software-reliant strategies. The ASF is designed to proactively enable system security and resilience engineering all through the lifecycle and supply chain. It provides a roadmap for setting up security and resilience proper right into a system, fairly than attempting in order so as to add it as quickly because the system has deployed. The ASF paperwork broadly used security and resilience practices and offers organizations a pathway for proactive course of administration integration. This twin cope with apply and course of produces an atmosphere pleasant and predictable acquisition and enchancment setting, which lastly leads to diminished security and resilience risks in deployed strategies.
These practices are associated it does not matter what acquisition and enchancment technique is chosen. Nonetheless, the place and the best way the practices are carried out—and by whom—can fluctuate broadly. Which components are acquired, and who makes the alternatives and integrates them into the system, shall be distinctive for each acquisition, nonetheless the need to deal with present chain hazard and deal with vulnerabilities will exist for each experience acquired.
The ASF helps shopping for organizations correlate administration of supply-chain hazard all through the quite a few components of their strategies, along with {{hardware}}, group interfaces, software program program interfaces, and mission capabilities. The ASF helps organizations incorporate security and resilience practices into the system lifecycle by
- defining a risk-based framework that
- provides a roadmap for managing security and resilience practices all through the system lifecycle
- manages complexity by way of elevated consistency and collaboration
- adapting system and software program program engineering measurement actions to include security the place acceptable
- supporting quite a few cyber-focused necessities, authorized tips, and guidelines with which all packages and strategies ought to comply
The ASF practices will likely be categorized into the subsequent six apply areas:
- program administration
- engineering lifecycle
- supplier dependency administration
- help
- unbiased analysis and compliance
- course of administration
Inside each of these apply areas are two to three domains. Inside each space, there are six or further targets, each with a bunch of practices that help an organization in meeting each function. The practices are phrased as questions that may be utilized in determining and evaluating current and deliberate organizational capabilities. Presently, now we’ve got accomplished the occasion of 4 of the six apply areas.
For the Engineering Lifecycle apply house, we acknowledged the subsequent domains:
- Space 1: Engineering Infrastructure
- Space 2: Engineering Administration
- Space 3: Engineering Actions
For Supplier Dependency Administration, we acknowledged the subsequent domains:
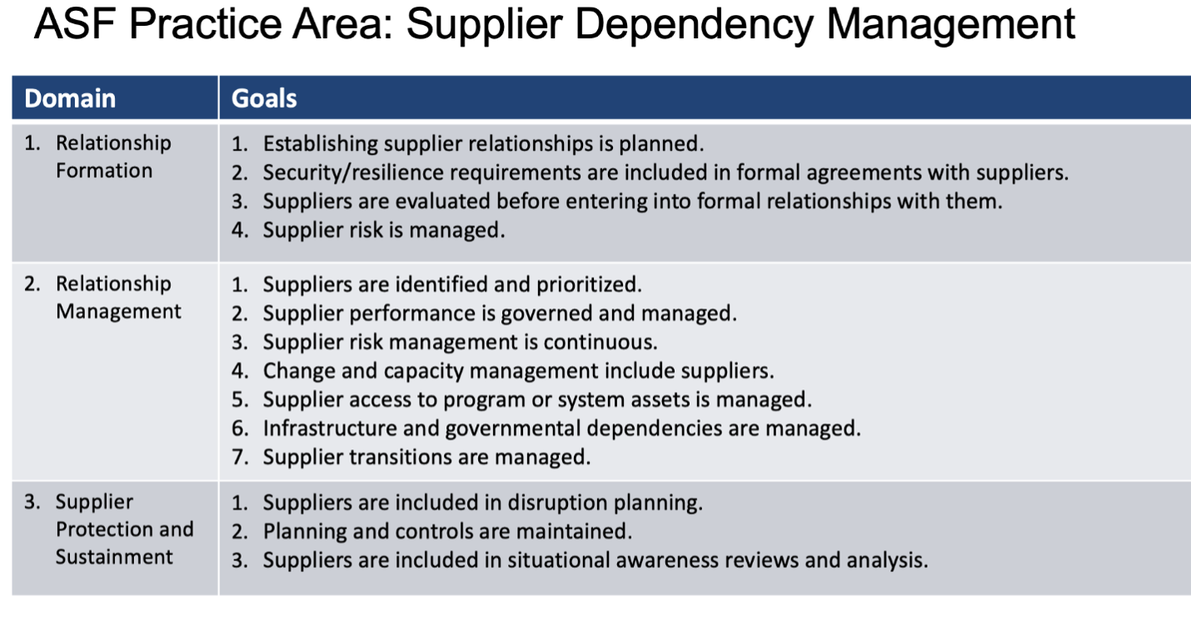
- Space 1: Relationship Formation
- Space 2: Relationship Administration
- Space 3: Supplier Security and Sustainment
For Program Administration, we acknowledged the subsequent domains:
- Space 1: Program Planning and Administration
- Space 2: Requirements and Hazard
For Assist, we acknowledged the subsequent domains:
- Space 1: Program Assist
- Space 2: Security Assist
Inside the the remainder of this submit, we’re going to take a look at the details for the second house, Supplier Dependency Administration. Although now we’ve got narrowed the primary goal for the wants of this weblog submit, I stress that to implement environment friendly supply-chain hazard administration, organizations ought to take into consideration all 4 apply areas.
ASF Observe House: Supplier Dependency Administration
Present chain cyber risks stem from a variety of dependencies, and particularly from the processing, transmittal, and storage of information, along with from data and communications experience. Each of these cyber risks contained in the present chain is broad and very important. Mandatory mission capabilities will likely be undermined by an adversary’s cyber assault on third occasions, even in circumstances the place an shopping for group is not explicitly contracting for experience or firms, just like information web internet hosting.
As confirmed in Desk 1 underneath, the world of Supplier Dependency Administration, the ASF identifies specific domains for each supplier that organizations ought to take into consideration when making a cybersecurity method to deal with present chain hazard.
Each of those targets then introduces quite a few questions that may help organizations tailor a present chain hazard administration technique to their program. The subsequent reveals the exact questions assigned to Space 1: Relationship Formation.
[ad_2]